The 7-Minute Rule for Risk Management Enterprise
Table of ContentsWhat Does Risk Management Enterprise Mean?Rumored Buzz on Risk Management EnterpriseHow Risk Management Enterprise can Save You Time, Stress, and Money.The 6-Second Trick For Risk Management EnterpriseWhat Does Risk Management Enterprise Mean?The Only Guide to Risk Management EnterpriseGetting The Risk Management Enterprise To Work
Below are some of its essential features that facilities should know. So, take a look. Real-Time Danger Assessments and Reduction in this software application permit organizations to continuously check and review dangers as they progress. This feature leverages real-time data and automatic analysis to identify prospective risks immediately. As soon as threats are determined, the software application promotes prompt reduction actions.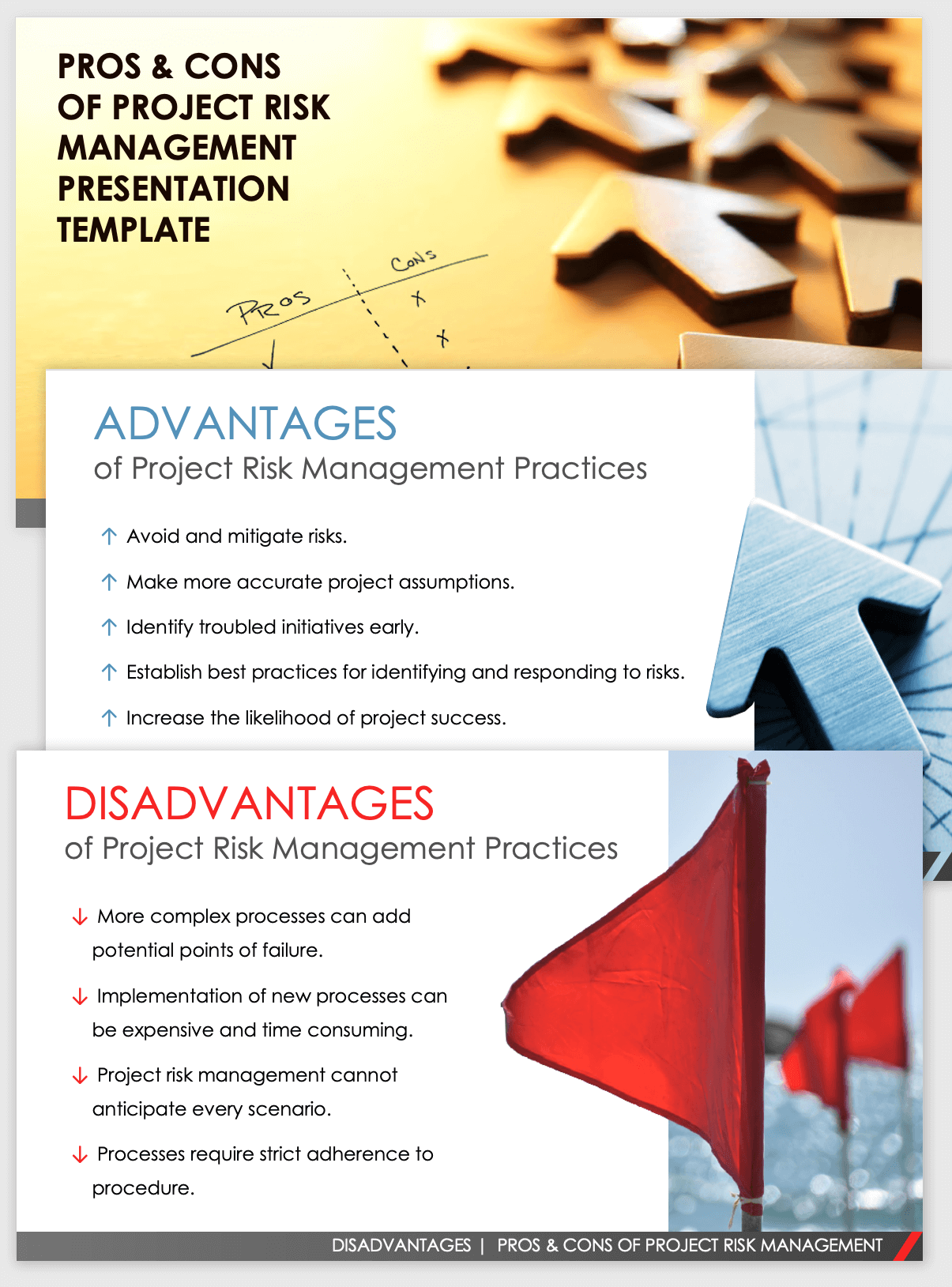
They deal with the challenge of recurring threat monitoring by offering tools to check dangers continuously. KRIs boost safety risk oversight, guaranteeing that potential dangers are determined and handled efficiently.
The 8-Second Trick For Risk Management Enterprise
IT run the risk of administration is a part of venture risk administration (ERM), made to bring IT run the risk of in line with a company's danger appetite. IT risk management (ITRM) includes the policies, treatments and modern technology necessary to lower threats and vulnerabilities, while keeping conformity with relevant regulatory needs. In enhancement, ITRM looks for to restrict the repercussions of devastating occasions, such as safety violations.
Veronica Rose, ISACA board director and an info systems auditor at Metropol Corp. The ISACA Risk IT framework aligns well with the COBIT 2019 structure, Rose claimed.
Enterprise Danger Management Software Program Growth: Conveniences & Qualities, Expense. With technological advancements, threats are constantly on the rise., services navigate with a continuously altering sea of dangers.
The Greatest Guide To Risk Management Enterprise
In this blog, we will certainly study the globe of ERM software application, exploring what it is, its advantages, features, etc to ensure that you can construct one for your business. Venture Threat Management (ERM) software program is the application program for planning, routing, organizing, and managing company tasks and streamlining danger monitoring processes.
With ERM, companies can make informative choices to enhance the general durability of the business. Committed ERM systems are vital for organizations that routinely deal with substantial amounts of delicate information and numerous stakeholders to approve critical choices.
It can be stayed clear of by using the ERM software system. This system automates regulation compliance management to maintain the company protected and certified.
The Best Strategy To Use For Risk Management Enterprise
You can likewise connect existing software systems to the ERM by means of APIs or by including data by hand. Companies can use ERM to examine threats based on their potential effect for far better risk monitoring and mitigation.: Including this function enables individuals to get real-time notifications on their tools concerning any risk that could take place and its influence.
Instead, the software allows them to establish limits for various processes and send push notices in situation of possible threats.: By integrating information visualization and reporting in the personalized ERM software program, services can gain clear insights regarding danger fads and performance.: It is mandatory for companies to comply with sector compliance and regulative standards.
These systems allow firms to implement best-practice danger monitoring procedures that straighten with market standards, providing an effective, technology-driven approach to recognizing, assessing, and mitigating threats. This blog discovers the advantages of automated danger administration devices, the areas of danger monitoring they can automate, and the worth they bring to a company.
Unknown Facts About Risk Management Enterprise
Groups can establish forms with the relevant fields and easily develop different kinds for different threat types. These risk assessment types can be flowed for completion through automated process that send out notifications to the appropriate team to finish the forms online. If types are not finished by the deadline, then chaser e-mails are immediately sent out by the system.
The control surveillance and control testing process can additionally be automated. Companies can use automated operations to send normal control test notifications and personnel can enter the outcomes through online types. Controls can likewise be monitored by the software application by setting rules to send alerts based on control data kept in other systems and spread sheets that is pulled right into the system by means of API integrations.
Threat administration automation software can additionally support with threat reporting for all degrees of the enterprise. Leaders can check out records on risk direct exposure and control performance through a selection of reporting outputs consisting of static reports, Power BI interactive records, bowtie evaluation, and Monte Carlo simulations. The ability to draw live reports at the touch of a button removes difficult data manipulation tasks leaving danger teams with more time to analyze the data and recommend business on the best strategy.
The need for efficient has never been more pressing. Risk Management Enterprise. Organizations operating in competitive, fast-changing markets can not manage hold-ups or inefficiencies in dealing with potential dangers. Typical threat administration utilizing hand-operated spreadsheet-based processes, while acquainted, typically lead to fragmented data, time-consuming coverage, and a raised likelihood of human error. Automating the threat management process with software addresses these drawbacks.
Unknown Facts About Risk Management Enterprise
This makes certain risk signs up are always existing and aligned with organizational purposes. Conformity is one more important motorist for automating risk management. Standards like ISO 31000, CPS 230 and COSO all offer assistance around danger administration finest methods and control frameworks, and automated threat administration tools are structured to straighten with these needs helping companies to fulfill most frequently used threat administration standards.
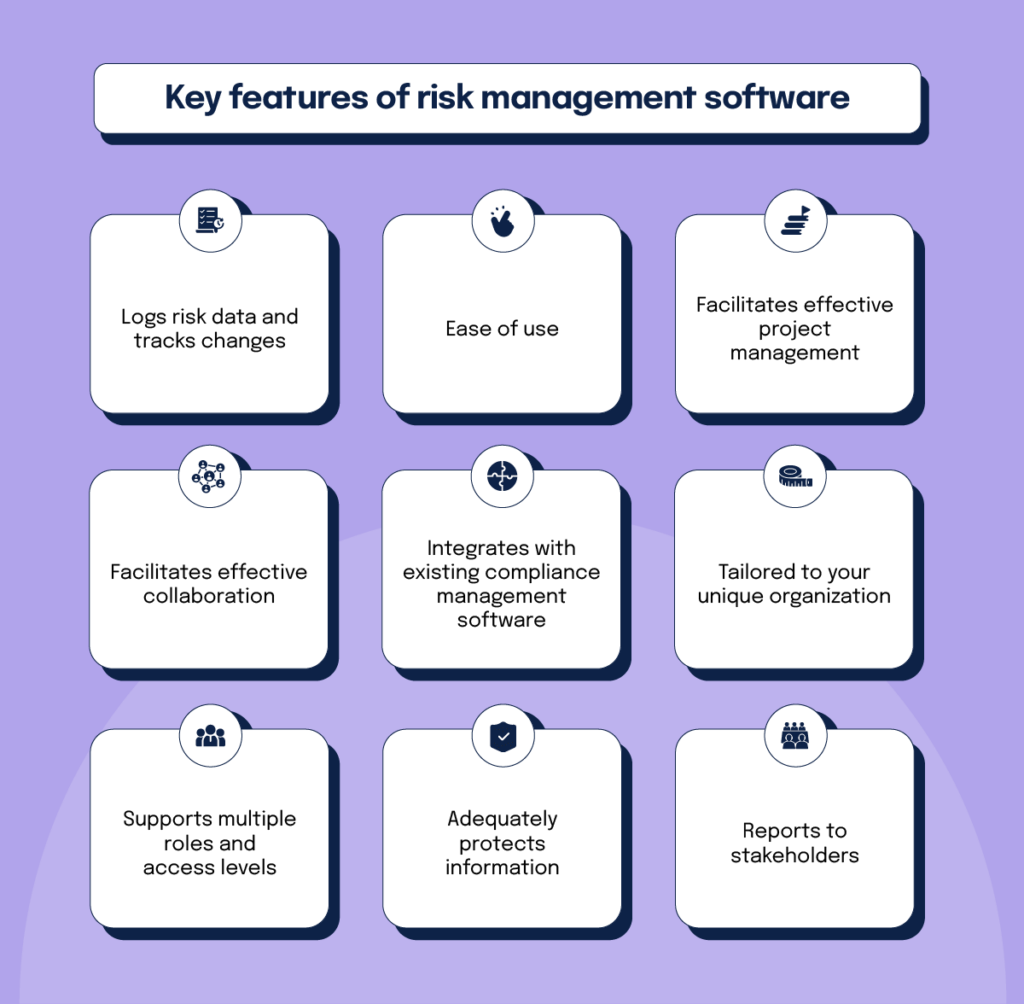
Try to find about his risk software program platforms with a permissions power structure to easily establish up process for risk rise. This functionality allows you to customize the view for each user, so they just see the information appropriate to them. Make sure the ERM software offers customer tracking so you can see who entered what information and when.
Choose a cloud-based platform to ensure the system obtains normal updates from the supplier including new capability. Seek devices that offer job threat monitoring capabilities to handle your tasks and portfolios and the connected threats. The advantages of taking on risk administration automation software extend far beyond performance. Companies that integrate these remedies into their ERM method can anticipate a host of tangible and abstract.
The Of Risk Management Enterprise
While the case for automation is compelling, carrying out a danger administration platform is not without its difficulties. To conquer the difficulties of danger monitoring automation, companies should spend in information cleansing and governance to make certain a strong structure for executing an automated platform.
Automation in threat monitoring equips organizations to change their strategy to take the chance of and build a stronger foundation for the future (Risk Management Enterprise). The inquiry is no more whether to automate risk monitoring, it's how soon you can start. To see the Riskonnect in action,
The solution often depends on exactly how well risks are prepared for and handled. Job management software functions as the navigator in the tumultuous waters of task execution, offering devices that determine and assess dangers and develop strategies to minimize them successfully. From real-time data analytics to comprehensive risk monitoring dashboards, these devices give a 360-degree sight of the project landscape, allowing job supervisors to investigate this site make enlightened choices that maintain their projects on course and within budget.